Linkerd vs. Istio: 7 Key Differences
What is Linkerd?
- Linkerd is an open source network proxy developed by Buoyant, which is commonly used as a service mesh solution. It supports platforms such as Docker and Kubernetes.
- Linkerd is designed to solve the challenges of operating and managing containerized workloads at large scale, in particular interactions between services.
- Linkerd provides an abstraction layer that helps control this communication, giving developers more visibility and reliability about the way services communicate with each other.
Linkerd vs. Istio: 7 Key Differences
What is Linkerd?
- Linkerd is an open source network proxy developed by Buoyant, which is commonly used as a service mesh solution. It supports platforms such as Docker and Kubernetes.
- Linkerd is designed to solve the challenges of operating and managing containerized workloads at large scale, in particular interactions between services.
- Linkerd provides an abstraction layer that helps control this communication, giving developers more visibility and reliability about the way services communicate with each other.
How Does Istio Work?
The Istio service mesh is divided into a data plane and a control plane:
- The data plane consists of a set of intelligent proxies (based on the Envoy open source project), deployed as sidecars alongside the application.
- The control plane manages and configures proxies to route traffic.
Image Source: Istio
Key Istio components include:
- Envoy proxy—a high performance proxy that routes inbound and outbound traffic for services in the service mesh. It is deployed as a sidecar alongside the relevant service in the same Kubernetes pod.
- Pilot—communicates with the Envoy proxy using the Envoy API. It manages traffic, handles routing, and performs service inspection.
- Citadel—enables secure inter-service communication, handling user authentication and managing certificates and credentials.
- Galley—manages configurations, processes them, and distributes them to Envoy proxies.
Learn more in our detailed guide to Istio architecture
How Does Linkerd Work?
Like Istio, Linked has two operational planes:
- The control plane—a set of services that control the Linkerd infrastructure.
- The data plane—sidecar containers running alongside service containers, with a component known as linkerd2-proxy, written in Rust. The proxy container handles TCP traffic to and from each service, and receives configuration from the control plane.
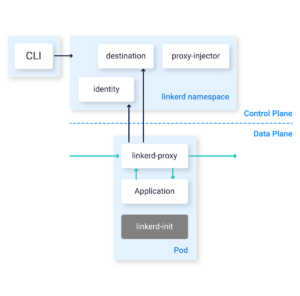
Image Source: Linkerd
The Linkerd control plane consists of several services that run in their own Kubernetes namespace (called linkerd by default). It has the following sub-components:
- Destination service—used by data plane proxies to determine their desired behavior. It receives service discovery details, fetches policy data about requests that should be allowed for each service, receives service profile data for route metrics, and handles retries and timeouts.
- The identity service—functions as a transport layer security (TLS) certificate authority. Accepts certificate signing requests (CSRs) from data plane proxies and provides signed certificates that can be used for secure proxy-to-proxy connections supporting mutual TLS (mTLS).
- The proxy injector—a Kubernetes admission controller that is triggered by a webhook each time a new pod is created in the cluster. When a new pod is created, the injector checks if resources have a Linkerd-specific annotation, and injects a proxy container into the pod.
Linkerd provides a CLI that can be used to interact with the control and data planes.
Istio vs. Linkerd: 7 Key Differences
1. Architecture
Both products use a similar architecture. They separate the control plane, which manages route data at the cluster level, from the data plane, which represents the functions and processes that transfer data from one interface to another on the service mesh.
Both use a “sidecar” mode, allowing agents to run in separate containers within each pod. The sidecar container sends and receives data to and from the application. It is responsible for transferring data to other pods or to destinations outside the cluster.
The key difference is the proxy used to perform this function:
- Istio uses the Envoy proxy, a de-facto industry standard with a community with 300+ companies making contributions.
- Linkerd 2.0 uses linkerd-2 as its proxy which has minimal industry support
2. Ingress
An ingress manages incoming traffic flowing into a Kubernetes cluster:
- Istio uses Envoy as the ingress. It provides solid functionality and was specifically designed for cloud native and Internet-scale API environments.
- Linkerd requires deploying a third-party controller such as NGINX to enable certain features such as rewriting incoming headers.
3. Egress
An egress controls outbound traffic from a cluster:
- Istio controls outbound traffic using virtual service objects and gateways.
- Linkerd enables egress management but it is not straightforward and can only be achieved through DNS and delegation tables (DTAB).
4. Performance and Scalability
Depending on the application architecture, scalability requirements and configuration, Istio and Linkerd perform similarly, but Istio is deployed and proven in much larger environments:
- Istio uses Envoy proxy which is written in C++ and offers excellent performance.
- Linkerd uses a Rust-based micro proxy called Linkerd2-proxy, which drives the entire data plane and offers good performance in smaller environments.
5. Security
Both products have good native support for certificate rotation and external root certificates. Beyond this:
- Istio provides generally superior security features, including HTTP and TCP support for mutual TLS (mTLS). In terms of policy management, Istio allows various providers to integrate their products into its policy management framework, and supports setting rules to limit which applications can communicate with each other.
- Linkerd supports mTLS by default for all TCP connections.
6. Monitoring
- Istio provides monitoring through a tight integration with Kiali. Kiali is an observability tool that can generate metrics, infer network topology, and integrate with Grafana for advanced query capabilities.
- Linkerd provides out-of-the-box Grafana dashboards that provide insights into service communications.
7. Community Support
- Istio has a strong community backed by major companies like Google, IBM and Lyft.
- Linkerd has limited community support. It was created by Buoyant, which is currently the main corporate sponsor for Linkerd.
The Need for an Istio Management Plane
Istio Pros and Cons
Istio pros:
- Built on widely supported industry standards like Envoy, which is the most mature, comprehensively supported solution on the market.
- Backed by a large community committing significant enhancements to to project
- Supports both Kubernetes, virtualized environments and bare metal.
- Free community support from many organizations and vendors
- Provides insight into network performance issues.
- Secures inter-service and inter-pod communication.
- Enables canary deployment and A/B testing.
Istio cons:
- Offers extensive features and customizations which can be daunting for new users
- Requires YAML configuration to ensure encrypted communication
Linkerd Pros and Cons
Linkerd pros:
- Provides extensive documentation
- Simplified feature set makes it easy to install and setup
Linkerd cons:
- Only backed by a single company with limited updates
- Only supports Kubernetes
- Missing some network routing features like circuit breaking and rate limiting
- Does not support security features like TCP for mTLS
- Does not have built-in ingress and egress
Commercial versions of Istio
Beyond the open source version of Istio, many vendors offer commercial versions of Istio which provide Istio users with:
- Enhanced Istio lifecycle management
- Extended features like enhancements like federated multi-cluster & hybrid support, multi-tenancy, pre-built extensions and FIPs compliance
- Production support including and SLAs for vulnerability fixes
- Backporting of patches and CVEs to older versions of Istio
For many organizations, the additional features, as well as the support and guidance offered by a commercial Istio provider like Solo.io, ensure a successful Istio implementation.

